Difference between revisions of "Networking"
Adelo Vieira (talk | contribs) (→Lab 1: Configuring Wireless Access and Security) |
Adelo Vieira (talk | contribs) (→Wireless networks) |
||
| Line 605: | Line 605: | ||
Note que algunos de estos términos (notablemente LAN y WAN) son empleados no sólo en Wireless technologies. Podemos, por supuesto, hablar de Wired LAN or Wired WAN. | Note que algunos de estos términos (notablemente LAN y WAN) son empleados no sólo en Wireless technologies. Podemos, por supuesto, hablar de Wired LAN or Wired WAN. | ||
| + | |||
| + | ===What wireless channel and frequency is a Network on=== | ||
| + | Using the software LinSSID, we performed a scan of the wireless networks in my house. In Figures are shown the results for 2.5GHz Channels. We can see our home network (iptime) is on channel 6 and its frequency is 2.437GHz: | ||
| + | |||
| + | XXXXXXXXXXXXXXXXXXX | ||
| + | |||
| + | ===What version of IP address do clients on the network receive fromt he ISP=== | ||
| + | * Where did you receive this IP address from? | ||
| + | |||
| + | In order to know what version of IP address receive clients on the network, we need to know the public IP address, which is the IP address provided for the ISP. The public IP address can be displays with a simple Google search.That is, entering “My IP address on our web search engine. There are many Web sites that are able to provide the public IP. In Fig. 3.4 is shown the result obtained in my case.The Linux command«curl»provide another way of knowing the public IP address: | ||
| + | |||
| + | curl ipinfo.io/ip | ||
| + | |||
| + | The results show that clients on the network receive IPv4 from the ISP. | ||
| + | |||
===Wireless LANs (WLANs)=== | ===Wireless LANs (WLANs)=== | ||
Revision as of 17:08, 5 November 2019
Contents
- 1 Resumen para el examen de Network Service Management and Virtualisation
- 2 Sistema binario
- 3 Terminología
- 4 TCP/IP
- 5 Introduction to Internetworking and Network equipments
- 6 IP addressing
- 7 Configuring basic router settings
- 8 WAN (Wide Area Network)
- 9 Routing
- 10 Wireless networks
- 11 Para ver las características de las tarjetas de red (network card)
- 12 DHCP
- 13 DNS
- 14 Using Wireshark to observe traffic
- 15 Network simulation using Cisco-PacketTracer
- 15.1 Cisco - PacketTracer
- 15.2 Configuration más frecuentes using PacketTracer
- 15.3 Lab 1: Configuring Wireless Access and Security
- 15.4 Lab 4: Configuring basic router settings with the Cisco IOS CLI
- 15.4.1 Configuring basic router settings
- 15.4.1.1 Configure a host name
- 15.4.1.2 Configure a console password and enable login
- 15.4.1.3 Configure the password on the vty lines
- 15.4.1.4 Configure the enable and enable secret passwords
- 15.4.1.5 Configure a message-of-the-day (MOTD) banner
- 15.4.1.6 Configure the router to not attempt to resolve host names using a DNS server
- 15.4.1.7 Console messages do not interfere with command input
- 15.4.1.8 Configure the serial interface
- 15.4.1.9 Display information about the serial interface
- 15.4.1.10 Configure the Fast Ethernet interface
- 15.4.1.11 Display information about the Fast Ethernet interface
- 15.4.1.12 Save the configuration
- 15.4.2 View the router running configuration
- 15.4.1 Configuring basic router settings
- 15.5 Lab 5: Configuring Challenge Handshake Authentication Protocol Bi-directional
- 15.5.1 Initial configuration of the Network
- 15.5.2 Define username and password to expect from the remote router
- 15.5.3 Configure the interface on for PPP encapsulation
- 15.5.4 See which ppp authentication options are available
- 15.5.5 Now configure for CHAP authentication
- 15.5.6 Troubleshooting / debugging
- 15.6 Lab 6: Configuring and verifying static routes
- 15.7 Lab: Dynamic routing
- 15.8 Configuring DHCPv4 on a Router
- 15.8.1 Part 1: Build the Network and Configure Basic Device Settings
- 15.8.1.1 Cable the network as shown in the topology
- 15.8.1.2 Initialize and reload the routers and switches
- 15.8.1.3 Add serial interfaces
- 15.8.1.4 Configure basic settings for each router
- 15.8.1.5 Configure the IPv4 addresses on the router as shown in the topology
- 15.8.1.6 Configure dynamic, default, and static routing on the routers
- 15.8.1.7 Verify network connectivity between the routers
- 15.8.1.8 Verify the host PCs are configured for DHCP
- 15.8.2 Part 2: Configure a DHCPv4 Server and a DHCP Relay Agent
- 15.8.1 Part 1: Build the Network and Configure Basic Device Settings
Resumen para el examen de Network Service Management and Virtualisation
Media:Resumen para el examen networking.pdf
- DHCP
- DNS
- ARP
- TCP
- HTTP
Some important questions that you should know:
- A network manager asks you to write down the steps for a DNS query when you open your browser and type www.google.com
- The network manager then asks you to describe the difference between a recursive and iterative query
- What typical transport layer protocol and port does DNS use for DNS lookups
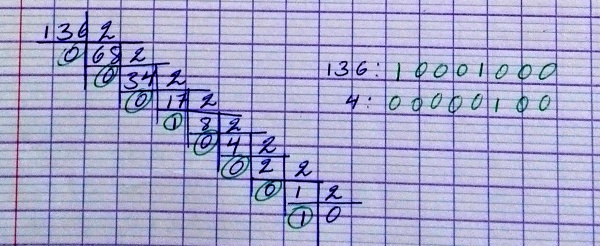
Sistema binario
Conversión de un número en el sistema decimal al binario:
Conversión de Binario a decimal:
Terminología
Protocols
Think of protocols as a standard way of communication between a client and a server.
LAN
A Local Area Network is a computer network that interconnects computers within a limited area such as a residence, school, laboratory, university campus or office building. https://en.wikipedia.org/wiki/Local_area_network
WAN
A Wide Area Network is a telecommunications network or computer network that extends over a large geographical distance. https://en.wikipedia.org/wiki/Wide_area_network
Puertos
- The wireless router’s WAN (Internet) port (el puerto WAN (Internet) del wireless router).
- The wireless router’s LAN (Ethernet) ports.
- RS-232: is a standard for serial communication transmission of data. https://en.wikipedia.org/wiki/RS-232
Elegir el puerto correcto
- Cuando se conecta un cable a una PC en Packet Tracer, el programa propone (por defecto) conectarlo al puerto FastEthernet, USB o RS-232. Hasta ahora hemos estado usando el puerto FastEthernet.
- Cuando se conecta un cable a un Router, PacketTracer propone el puerto Internet o Ethernet. Creo que el puerto Internet se usa cuando estamos conectando el Router con una WAN y el Ethernet es para una LAN.
Cables
- As a rule, between different divices we use a straight cable an between same divices a cross-over cable (Creo que el Prof. confirmó esto, no estoy seguro)
- Crossover cable:
- From a PC to the wireless router’s WAN (Internet) port.
- Straight through cable:
- From PC to one of the wireless router’s LAN (Ethernet) ports.
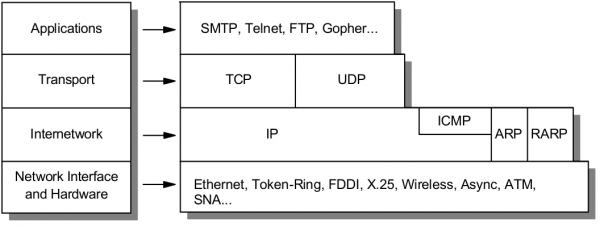
TCP/IP
https://en.wikipedia.org/wiki/Internet_protocol_suite
The Internet protocol suite is the conceptual model and set of communications protocols used on the Internet and similar computer networks.
The Internet protocol suite provides end-to-end data communication specifying how data should be packetized, addressed, transmitted, routed, and received. This functionality is organized into four abstraction layers which classify all related protocols according to the scope of networking involved. From highest to lowest, the layers are:
- The application layer: it provides process-to-process data exchange for applications. HTTP, FTP, DNS etc.
- The transport layer: handling host-to-host communication. TCP, UDP, etc.
- The internet (Internetwork) layer: providing internetworking between independent networks. IP (IPv4, IPv6), etc.
- Network interface and Hardware [Datalink, Physical] layer: containing communication methods for data that remains within a single network segment (link). Ethernet, Wireless, etc.
Applications
HTTP
The HTTP request. HTTP is the pull protocole. A client pulls a page from the server.
FTP
DNS
Transport
TCP
TCP (Transmision Control Protocol)
Internetwork
IP
Network interface and Hardware [Datalink, Physical]
Ethernet
Wireless
OSI model
https://en.wikipedia.org/wiki/OSI_model#Comparison_with_TCP.2FIP_model
| OSI Model | ||||
|---|---|---|---|---|
| Layer | Protocol data unit (PDU) | Function | ||
| Host layers |
7. Application | Data | High-level APIs, including resource sharing, remote file access | |
| 6. Presentation | Translation of data between a networking service and an application; including character encoding, data compression and encryption/decryption | |||
| 5. Session | Managing communication sessions, i.e. continuous exchange of information in the form of multiple back-and-forth transmissions between two nodes | |||
| 4. Transport | Segment (TCP) / Datagram (UDP) | Reliable transmission of data segments between points on a network, including segmentation, acknowledgement and multiplexing | ||
| Media layers |
3. Network | Packet | Structuring and managing a multi-node network, including addressing, routing and traffic control | |
| 2. Data link | Frame | Reliable transmission of data frames between two nodes connected by a physical layer | ||
| 1. Physical | Bit | Transmission and reception of raw bit streams over a physical medium | ||
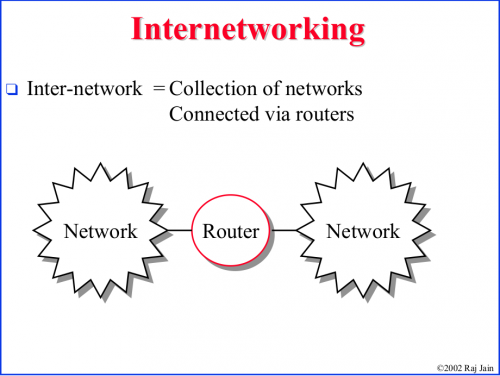
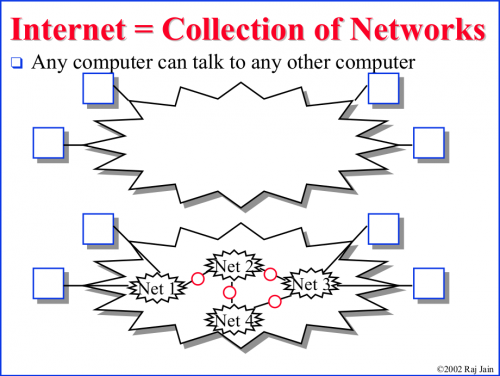
Introduction to Internetworking and Network equipments
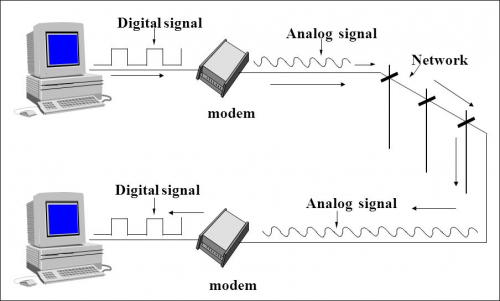
Modem
https://www.webopedia.com/TERM/M/modem.html
http://homepages.uc.edu/~thomam/Net1/Modems%20&%20D-A%20Conversion/modem_main.html
A modem (Short for modulator-demodulator) is a device or program that convert digital information to analog signals (modulation), and to convert analog signals back into useful digital information (demodulation). It enables a computer to transmit data over, for example, telephone or cable lines. http://homepages.uc.edu/~thomam/Net1/Modems%20&%20D-A%20Conversion/modem_main.html
Computer information is stored digitally, whereas information transmitted over telephone lines is transmitted in the form of analog signal. A modem converts between these two forms.
Router
http://www.diffen.com/difference/Router_vs_Switch
Router and switches are both computer networking devices that allow one or more computers to be connected to other computers, networked devices, or to other networks.
The functions of a routers, switch and hub are all different, even if at times they are integrated into a single device.
Routers can connect wired or wireless (WiFi) networks. A switch is used for wired networking connections.
A router is a networking device that connects computer networks (connect two or more logical subnets). For example, connecting a home network with the Internet.
Routers operate at Layer 3 (network layer) of the OSI model. They direct traffic and perform other functions to efficient network operation. For example, they receive TCP/IP packets, look inside each packet to identify the source and target IP addresses, then forward these packets as needed to ensure the data reaches its final destination.
In addition, routers often perform network address translation (NAT), which allows all devices on a subnetwork (e.g., all devices in a home) to share the same public IP address.
Como se mencionó arriba, routers can connect wired or wireless (WiFi) networks.
Existen diferentes tipos de Routers. El uso y la manera de configurarlos varía notablemente:
The largest routers (such as the Cisco CRS-1 or Juniper PTX) interconnect the various ISPs, or may be used in large enterprise networks. Smaller routers usually provide connectivity for typical home and office networks. https://en.wikipedia.org/wiki/Router_(computing)
Al parecer se habla también Wireless Routers. Creo sin embargo que este dispositivo sería un Router equipado con un AP y una tarjeta de red wireless.
En el Lab 1 se realiza un modelado de networks en el cual se emplea un Wireless Router. Este Wireless Router podría, por ejemplo, representar el Router que se encuentra integrado en la Box de nuestra home network. En el Lab 1, note que en este Router las configuraciones se ralizan a través de un GUI.
En el Lab 4: Configuring basic router settings with the Cisco IOS CLI, se presenta un modelado de network en el cual se emplea un Router Cisco. Note que este tipo de Routers son configuring with the Cisco IOS CLI (línea de comandos).
Switch
A network switch is a computer networking device that is used to connect many devices together on a single computer network (within one local area network (LAN)).
Switches are incapable of joining multiple networks or sharing an Internet connection.
A switch is also called switching hub, bridging hub, or MAC bridge. Switches use MAC addresses to forward data to the correct destination. A switch is considered a Layer 2 device, operating at the data link layer; switches use packet switching to receive, process and forward data.
A switch is considered more advanced than a hub because a switch will on send msg to device that needs or request it
Access point
The Access Point (AP) is the central node in 802.11 wireless implementations. It is the interface between wired and wireless network
An access point is a hardware device that receives data by wired Ethernet and, using 2.4GHz or 5GHz radio waves bands, converts to a wireless signal. It sends and receives wireless traffic to and from nearby wireless clients.
For a home environment, most often you have a router, a switch, and an AP «embedded in one box (into a single device)», making it really usable for this purpose.
IP addressing
IP address
Dirección IP
Classful network
Clases de public IP addresses
| Classe | Bits de départ | Début | Fin | Notation CIDR | Masque de sous-réseau par défaut |
|---|---|---|---|---|---|
| Classe A | 0 | 0.0.0.0 | 127.255.255.255 | /8 | 255.0.0.0 |
| Classe B | 10 | 128.0.0.0 | 191.255.255.255 | /16 | 255.255.0.0 |
| Classe C | 110 | 192.0.0.0 | 223.255.255.255 | /24 | 255.255.255.0 |
| Classe D (multicast) | 1110 | 224.0.0.0 | 239.255.255.255 | non défini | |
| Classe E (réservée) | 1111 | 240.0.0.0 | 255.255.255.255 | non défini |
Private IP Addresses
IP addresses reservadas para ser usadas como privadas:
10.0.0.0 – 10.255.255.255 172.16.0.0 – 172.31.255.255 192.168.0.0 – 192.168.255.255
IP Privado
ifconfig
ifconfig
Para obtener una nueva dirección IP en Windows se hace:
ipconfig /release ipconfig /renew
En Linux los comandos análogos son: https://www.cyberciti.biz/faq/howto-linux-renew-dhcp-client-ip-address/
To renew or release an IP address for the eth0 interface, enter:
sudo dhclient -r sudo dhclient
IP Público
curl ipinfo.io/ip
Command-line to list DNS servers used by my system
https://askubuntu.com/questions/152593/command-line-to-list-dns-servers-used-by-my-system
nmcli device show <interfacename> | grep IP4.DNS
Para desplegar el IP de la geteway
route -n
Subnet mask
IP/Subnet Calculator:
- http://jodies.de/ipcalc (Éste me pareció excelente)
- http://www.subnet-calculator.com/ (Éste no me gustó pero tiene una pestaña que permite seleccionar la Subnet Mask. En ella se presentan las Subnets comúnmente usadas.
La subnet mask que generalmente he estado usando para los ejemplos es la 255.255.255.0 (/24). Esta subnet mask indica que los primeros 24 bits de una IP deben ser iguales para pertenecer a la misma subnet. Esta en particular es muy fácil, y se puede ver fácilmente el rango de IP's que define. Por ejemplo:
- Si tenemos: 172.17.0.1/24, podemos fácilmente saber que: ( Ver http://jodies.de/ipcalc )
Address: 172.17.0.1 10101100.00010001.00000000 .00000001
Netmask: 255.255.255.0 = 24 11111111.11111111.11111111 .00000000
Wildcard: 0.0.0.255 00000000.00000000.00000000 .11111111
=>
Network: 172.17.0.0/24 10101100.00010001.00000000 .00000000 (Class B)
Broadcast: 172.17.0.255 10101100.00010001.00000000 .11111111
HostMin: 172.17.0.1 10101100.00010001.00000000 .00000001
HostMax: 172.17.0.254 10101100.00010001.00000000 .11111110
Hosts/Net: 254 (Private Internet)
- Ahora, en el caso de 172.17.0.1/27, las cosas no son tan evidentes:
Address: 172.17.0.1 10101100.00010001.00000000.000 00001
Netmask: 255.255.255.224 = 27 11111111.11111111.11111111.111 00000
Wildcard: 0.0.0.31 00000000.00000000.00000000.000 11111
=>
Network: 172.17.0.0/27 10101100.00010001.00000000.000 00000 (Class B)
Broadcast: 172.17.0.31 10101100.00010001.00000000.000 11111
HostMin: 172.17.0.1 10101100.00010001.00000000.000 00001
HostMax: 172.17.0.30 10101100.00010001.00000000.000 11110
Hosts/Net: 30 (Private Internet)
- 172.17.0.1/30
Address: 172.17.0.1 10101100.00010001.00000000.000000 01
Netmask: 255.255.255.252 = 30 11111111.11111111.11111111.111111 00
Wildcard: 0.0.0.3 00000000.00000000.00000000.000000 11
=>
Network: 172.17.0.0/30 10101100.00010001.00000000.000000 00 (Class B)
Broadcast: 172.17.0.3 10101100.00010001.00000000.000000 11
HostMin: 172.17.0.1 10101100.00010001.00000000.000000 01
HostMax: 172.17.0.2 10101100.00010001.00000000.000000 10
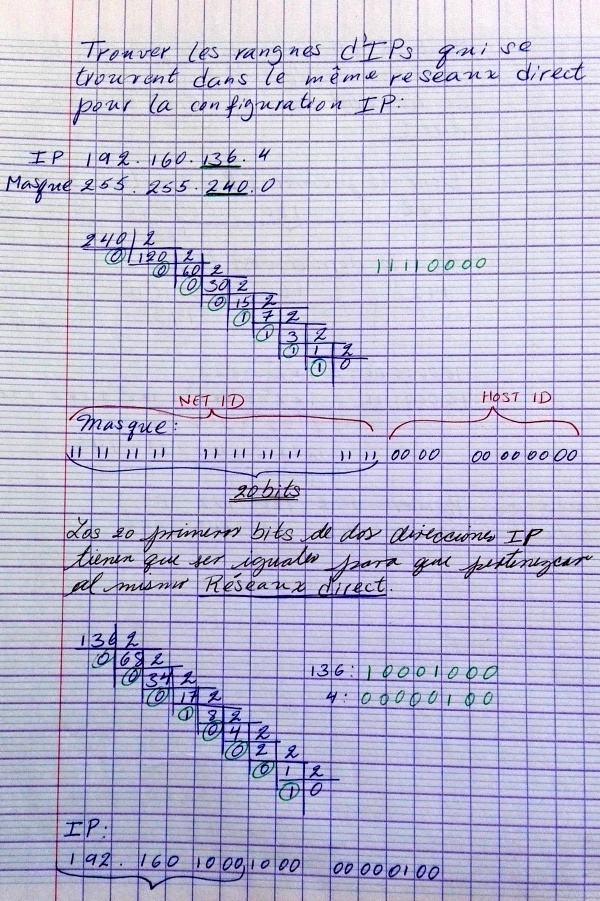
Hosts/Net: 2 (Private Internet)Definición de una subred
A través de la Máscara de subred se define que IPs forman parte del la misma Red (directa)
La notación 192.160.136.4/24 define una máscara de subred en donde los primeros 24 bits son 1 --> 255.255.255.0
Network address
Broadcast address
https://www.techopedia.com/definition/2384/broadcast-address
Gateway
El comando route: http://www.thegeekstuff.com/2012/04/route-examples
route
Internet speed
https://askubuntu.com/questions/104755/how-to-check-internet-speed-via-terminal
La velocidad de la conexión Internet se puede medir en kbit/s (Download/Upload)
Podemos usar el siguiente script en línea:
curl -s https://raw.githubusercontent.com/sivel/speedtest-cli/master/speedtest.py | python -
o instalar el programa usado en la linea de comando anterior (speedtest-cli) como se explica aquí: https://fossbytes.com/test-internet-speed-linux-command-line/
sudo apt-get install speedtest-cli OR
sudo apt-get install python-pip pip install speedtest-cli
To test internet speed, just type the following command and press enter:
speedtest-cli
You can find various options in the help section of the utility:
speedtest-cli -h
Display the internet speed in megabytes/sec:
speedtest-cli --bytes
También podemos obtener una medida a través de wget:
wget -O /dev/null http://speedtest.wdc01.softlayer.com/downloads/test10.zip
Desplegar la ruta de un paquete enviado en Internet
El comando traceroute permite optener la ruta de un paquete enviado.
traceroute google.com
En el ejemplo anterio podemos ver que el paquete pasa por el IP 109.255.255.254 (que debería ser el Gateway de mi ISP). En la página que muestro a continuación se pude ver que dicho IP pertenece a mi ISP y está ubicado en Cork.
Who is my ISP
Este sitio muestra ISP: https://www.whoismyisp.org/
Configuring basic router settings
WAN (Wide Area Network)
A Wide Area Network is a telecommunications network or computer network that extends over a large geographical distance.
Purpose of WANs:
- WANs connect LANs.
- WANs connect home users to the Internet.
- WANs are used to connect remote sites to the enterprise network.
- Enterprise networks are using security and privacy solutions over the Internet to connect remote sites and users.
Common WAN topologies are:
- Point-to-Point: Typically a dedicated leasedline connection (such as T1/E1)
- T1 (1.544 MB/s) and E1 (2.048 MB/s) are examples of synchronous TDM serial connections. (Note: T1 is the standard for the U.S and E1 is the standard for Europe). An E1 contains 32 DS0’s
- Hub-and-Spoke: A single-homed, point-tomultipoint topology where a single interface on the hub router can be shared with multiple spoke routers through the use of virtual interfaces
- Full Mesh: Each router has a connection to every other router; requires a large number of virtual interfaces
- Dual-homed: Provides redundancy for a single-homed, hub-and-spoke topology by providing a second hub to connect to spoke routers
Two way that a business can get WAN access:
- Private WAN Infrastructure: The business negotiates for dedicated or switched WAN access with a service provider.
- Public WAN Infrastructure: WAN access is achieved through the Internet using broadband connections.
- In this case, VPNs (virtual private networks) are used to secure the connections.
Private WAN Infrastructure:
- Ethernet WAN (Known as Metropolitan Ethernet (MetroE), Ethernet over MPLS (EoMPLS))
- Multiprotocol Label Switching (MPLS) is a multiprotocol high-performance WAN technology that directs data from one network node to the next based on short path labels rather than long network addresses, avoiding complex lookups in a routing table.
- MPLS allows most packets to be forwarded at Layer 2 (the switching level) rather than having to be passed up to Layer 3 (the routing level).
- With MPLS, the Layer 3 header analysis is done just once (when the packet enters the MPLS domain). Label inspection drives subsequent packet forwarding.
- MPLS provides these beneficial applications:
- Virtual Private Networking (VPN)
- Traffic Engineering (TE)
- Quality of Service (QoS)
Public WAN Infrastructures:
- DSL (Digital Subscriber Line)
- A DSL modem converts an Ethernet signal from the user device to a DSL signal, which is transmitted to the central office.
- Cable: Network access is available from some cable television networks.
- 3G/4G Wireless Abbreviation for 3rd generation and 4th generation cellular access.
- Public WANs rely on VPNs for securing data between private networks as it crosses a public network, such as the Internet.
- Two types of VPN:
- Site-to-site VPNs
- Remote-access VPNs
- Two types of VPN:
Routing
- When a packet enters a router, how does it know where to send it?
- The router first read the packet information:
- TTL: if this field remains greater than 0, the router forwards the packet, otherwise it discards it.
- Destination IP
- Then, the router look for its routing tables. The destination network of the IP packet have to be stored in its routing tables so the router can determine where to send it, otherwise it discards it.
- Based in the information read, the routing protocol
- What information does the router need to already have to send it?
- How do routers get this information?
- How long do they store it?
- What information does the router modify in the packet?
The main purpose of a router if to route IP packets. The router decides what to do with the packet (discards it or forward it (and in this case where to forward it)) based on:
- The information stored in the IP packet header, and
- The Routing table (routing information base) stored in a router.
IP packet
An IP packet consists of a header section and a data section.
The IPv4 packet header consists of 14 fields, of which 13 are required. The 14th field is optional and aptly named: options.
Una buena explicación del IPv4 packet header se encuentra en https://en.wikipedia.org/wiki/IPv4#Header
The fields in an IPv4 packet header are:
- Version identifies the IP version to which the packet belongs. E.g. IPv4.
- Header Length describes the length of the IP header in 32-bit words. The minimum length of the IP header is 20 octets.
- Type of Service is used to specify special handling of the packet. This field can be divided into two subfields:
- Precedence: Sets a priority for the packet.
- TOS: Allows the selection of a delivery service in terms of throughput, delay, reliability.
- Total Length describes the total length of the packet in octets.
- Identifier is used in conjunction with the Flags and Fragment Offset fields for fragmentation of a packet.
- Flags field has the first bit as unused. The second bit is the Don't Fragment (DF) bit.The third bit is the More Fragments (MF) bit indicating if the fragment is the last one or not.
- Fragment Offset specifies the offset, in units of eight octets, from the beginning of the header to the beginning of the fragment.
- time-to-live (TTL):
- Time-to-live (TTL) is a value in an Internet Protocol (IP) packet that tells a network router whether or not the packet has been in the network too long and should be discarded. In IPv6 the TTL field in each packet has been renamed the hop limit.
- An IP TTL is set initially by the system sending the packet. It can be set to any value between 1 and 255; different operating ystems set different defaults. Each router that receives the packet subtracts at least 1 from the count; if the count remains greater than 0, the router forwards the packet, otherwise it discards it and sends an Internet Control Message Protocol.
- Protocol describes Transport Layer protocol for which the information in the IP packet is destined.
- Header Checksum is the error detection field for the IP header. The checksum is not calculated for the Data inside IP packet.
- Source Address is the address of the originator of the packet.
- Destination Address is the address of the destination of the packet.
- Options field is an optional field used primarily for testing .
- Padding is used to ensure that the IP header ends on a 32-bit boundary by adding zeros after the Options field.
From the IP packet header, the router is particularly interested in:
- TTL:
- if TTL > 0 :
- TTL = TTL - 1;
- The router will try to forward the packet.
- Else : the packet will be descarted.
- if TTL > 0 :
- Destination Address: To determine (using the Routing table) where to forward the packet.
It is also important to note that as a packet travels from one networking device to another:
- The Source and Destination IP addresses NEVER change.
- The Source & Destination MAC addresses CHANGE as packet is forwarded from one router to the next.
The Routing table (routing information base)
It's a data table stored in a router that lists the routes (las rutas) to particular network destinations, and in some cases, metrics (distances) associated with those routes.
A routing table is basically a list of IP Addresses of the NETWORKS that this particular router knows. For each Network IP address there are other information that the Router uses to know where to forward a packet that have to reach a particular Network.
A routing table looks like this: https://en.wikipedia.org/wiki/Routing_table#Contents_of_routing_tables
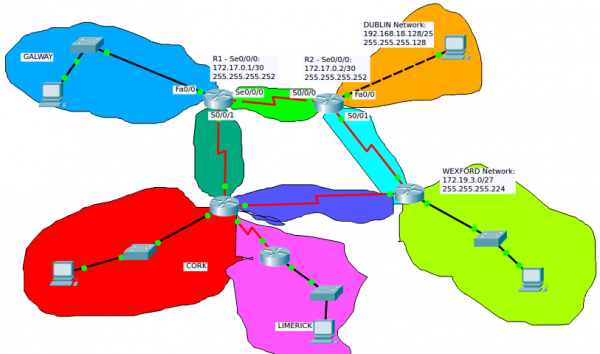
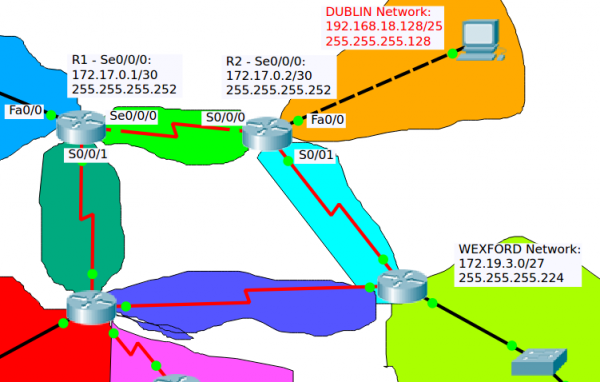
If we take, for example, one of the Networks listed in the routing table shown for the «show ip route» of the IOS CLI:
- R 192.19.3.0/27 [120/2] via 172.17.0.2, 00:00:26, Serial0/0/0
- R: RIP - Protocol used to generate this route.
- C: Directly connected network
- S: Static - Ruta ingresada manualmente (Static routing)
- 192.19.3.0/27: Netword Destination address and Netmask
- via 172.17.0.2: This is the IP Adress of the interface of the Router attached through which the network can be reached.
- Gateway or Next hop: it points to the gateway through which the network can be reached.
- Serial0/0/0 is the interface of the current Router that is attached to the gateway. That is, Serial0/0/0 is connected to 172.17.0.2
- 120: is the Administrative Distance
Static routing
Dynamic routing
Many IP routing protocols exist. However, they all have some core features in common:
- Learn routing information about IP subnets from other neighboring routers (discovery of remote networks).
- If a router learns of more than one router to reach one subnet, choose the best route based on that routing protocol’s concept of a metric (choose the best path)
- React to changes when the network topology changes e.g. when a link fails, and converge to use a new choice of best route for each destination subnet.
- Advertise routing information about IP subnets to other neighboring routers.
Routing Table Structure:
- A directly connected network is a network that is directly attached to one of the router interfaces.
- When a router interface is configured with an IP address and subnet mask, the interface becomes a host on that attached network.
- The network address and subnet mask of the interface, along with the interface type and number, are entered into the routing table as a directly connected network.
- When a router forwards a packet to a host, such as a web server, that host is on the same network as a router's directly connected network.
- A remote network is a network that is not directly connected to the router.
- Remote networks are added to the routing table using either a dynamic routing protocol or by configuring static routes.
- The network/exit-interface is the address of the local interface or the interface name that is in that network.
Example of routing protocols
- RIP (Routing Information Protocol)
- EIGRP (Enhanced Interior Gateway Routing Protocol)
- OSPF (Open Shortest Path First)
EIGRP is a Cisco proprietary routing protocol, whereas all other routing protocols listed are standard, non-proprietary protocols.
Administrative Distance (AD)
In some cases, internetworks use Multiple Routing Protocols. In such cases, a router learns of multiple routes to a particular subnet using different routing protocols. Which will be used? AD is used to rank routing protocols. AD is an integer from 0 to 255 that rates the trustworthiness of the source of the IP routing information.
| Route Source | Administrative Distance |
|---|---|
| Connected routes | 0 |
| Static routes | 1 |
| OSPF | 110 |
| IS-IS | 115 |
| RIP (V1 and V2) | 120 |
| Unknown/Unbelievable | 255 |
Wireless networks
Wireless Technologies:
- PAN/WPAN (Personal Area Network (PAN)/wireless personal area network (WPAN)
- Bluetooth, IEEE 802.15.4
- LAN (Local Area Network)
- IEEE 802.11
- MAN (Metropolitan Area Network)
- IEEE 802.11, IEEE 802.16, IEEE 802.20
- WAN (Wide Area Network)
- GSM, CDMA, Satelite, 3G, LTE
Note que algunos de estos términos (notablemente LAN y WAN) son empleados no sólo en Wireless technologies. Podemos, por supuesto, hablar de Wired LAN or Wired WAN.
What wireless channel and frequency is a Network on
Using the software LinSSID, we performed a scan of the wireless networks in my house. In Figures are shown the results for 2.5GHz Channels. We can see our home network (iptime) is on channel 6 and its frequency is 2.437GHz:
XXXXXXXXXXXXXXXXXXX
What version of IP address do clients on the network receive fromt he ISP
- Where did you receive this IP address from?
In order to know what version of IP address receive clients on the network, we need to know the public IP address, which is the IP address provided for the ISP. The public IP address can be displays with a simple Google search.That is, entering “My IP address on our web search engine. There are many Web sites that are able to provide the public IP. In Fig. 3.4 is shown the result obtained in my case.The Linux command«curl»provide another way of knowing the public IP address:
curl ipinfo.io/ip
The results show that clients on the network receive IPv4 from the ISP.
Wireless LANs (WLANs)
A WLAN is a Wireless Local Area Network, which is the linking of two or more computers without using wires. Instead, radio waves and IEEE 802.11 are used to communicate.
WLANs use infrared light (IR) or radio frequencies (RFs). The use of RF is far more popular for its longer range, higher bandwidth, and wider coverage.
Wireless LAN have to operate in the ISM (Industrial Scientific Medical) band.
Wireless LANs Primarily operate in the 2.4Ghz (2.401 - 2.483) & 5Ghz (5.470 - 5.725) frequency ranges. Basically a Higher frequency result in a greater speed but in a shorter range. That means 5Ghz waves cannot travel such great distances as 2.4Ghz waves but can carry more data. Also, the 5Ghz frequency is shared with less other unlicenced equipment.
Because the wireless transmission medium is shared, it is not possible to transmit in the exact same frequency without collisions (interference). The solution is to devide the ISM band into channels and map each WLAN/SSID on a single channel.
The 2.4 GHz range is devided into 11 channels. Each channel of 22MHz bandwidth (because we need 22MHz to transmit 54 Mbps in 802.11g) y una separación de 5MHz entre cada channel.
The most common arrangement is to use only channels 1, 6, and 11, which do not overlap with each other at all.
The 5-GHz (U-NII) band is much more flexible in this regard because it has many more non-overlapping channels available. In fact, all channels are spaced such that they will not overlap each other. Each U-NII channel is 20 MHz wide. With all four U-NII bands set aside for wireless LANs, a total of 23 non-overlapping channels are available.
Wireless technologies
- PAN/WPAN (Personal Area Network (PAN)/ Wireless Personal Area Network (WPAN)
- Bluetooth, IEEE 802.15.4
- LAN (Local Area Network)
- IEEE 802.11
WLAN Components
- Wireless Client Receiver:
- It is needed to connect a computing device (e.g. desktop, laptop, PDA…) to the wired networked via an access point. It includes Onboard Cards (most laptops) PCMCIA, PCI card or USB adaptor
- Access points (APs):
- They are needed only in the Infrastructure Mode of WLANs. They provide the wireless client with a point of access into a network. They are like Ethernet switches in a wired network and operate in half-duplex mode (e.g. They either receive or transmit at any given time).
- Wireless repeater:
- A wireless repeater (also called wireless range extender) takes an existing signal from a wireless router or wireless access point and rebroadcasts it to create a second network. When two or more hosts have to be connected with one another over the IEEE 802.11 protocol and the distance is too long for a direct connection to be established, a wireless repeater is used to bridge the gap. The throughput for client devices will be low because each repeater must receive and re-transmit each packet.
- Wireless bridge:
- A wireless bridge is a device used for connecting two or more network separated physically, operating on the 802.11 standard.
The WLAN supports four Network Topologies
- Peer-to-peer (Ad hoc) Topology: An ad hoc network is a type of temporary computer-to-computer connection. In ad hoc mode, you can set up a wireless connection directly to another computer without having to connect to a Wi-Fi access point or router.
- Hybrid Topology:
- Infrastructure Topology: All devices are connected to an access point.
- Point-to-point Topology: When we have two different networks connected by a Wirelless bridge.
802.11 standards
802.11 is the generic name of a family of standards for wireless networking. The numbering system for 802.11 comes from the IEEE (a nonprofit professional organization), who uses “802” for many networking standards like Ethernet (802.3).
The 802 committee supports in this model the LLC (logical link control), the MAC (media access control) and PHY (physical layers).
Popular 802.11 standards include 802.11a, 802.11b, 802.1g, 802.11n, 802.11ac (Newest)
Some EEE 802.11 standards are:
| Standard | Release Date | Frequency band | Max speed (Data Rate) | Max range | Comments |
|---|---|---|---|---|---|
| 802.11 | 1997 | 2.4 GHz | 2 Mbps | Undefined | Legacy |
| 802.11a | 1999 | 5 GHz | 54 Mbps | 50m | Not compatible with b, g / Expensive / Modulation: OFDM |
| 802.11b | 1999 | 2.4 GHz | 11 Mbps | 100m | First 2.4 GHz Technology / Modulation: DSSS |
| 802.11g | 2003 | 2.4 GHz | 54 Mbps | 100m | Backward compatible with b / Shares range with b / Modulation: OFDM, DSSS |
| 802.11n | 2011 | 2.4 or 5 GHz | 600 Mbps | 300m | Modulation: OFDM |
| 802.11ac | 2014 | 5 GHz | 1.3 Gbps | 300m | Newest Standard |
Wireless Security
Why secure the WLAN?
- Firstly, if someone manages to hack into your WLAN, they are stealing your bandwidth.
- Worse, anyone on your WLAN will be using the same Internet protocol (IP) address as you. To others on the Internet they appear to be you.
What security can you get now?
- The first being to change the default settings of your Access point:
- The most important is the Extended Service Set Identification (ESSID) (Network Name)
- You can configure the AP so that it doesn't broadcast (para que no muestre) the ESSID.
- The Extended Service Set Identification (ESSID) is one of two types of Service Set Identification (SSID).
- An SSID is a 32-character (maximum) alphanumeric key identifying the name of the wireless local area network. Some vendors refer to the SSID as the network name. For the wireless devices in a network to communicate with each other, all devices must be configured with the same SSID.
- In an infrastructure wireless network that includes an access point, the ESSID is used, but may still be referred to as SSID.
- In an Ad hoc wireless network with no access points, the Basic Service Set Identification (BSSID) is used.
- MAC address filters:
- There's a second layer of security you can adopt, the MAC (Media Access Control) address filter. A MAC address is a unique identity burned into every network adapter during manufacture, with no way of changing it. Using this filter, the AP maintains a list of MAC addresses and only permits those on the list to connect.
- Encryption:
- Even if hackers can't get past your AP, they may still be able to access data that's traversing your WLAN.
- The way to protect data in transit is encryption, the original WLAN encryption standard was WEP (Wired Equivalence Privacy).
- WEP works by encrypting traffic -scrambling it- as it leaves the AP or client PC and decrypting it on arrival.
- WEP has been replaced by WPA (Wifi Protected Access).
- Disable remote access to the router administration GUI:
- Make sure you only configure the AP over a wired connection.
- To remotely log into your router's administrative console you just have to open a browser window and typing the router IP address.
- Your router is likely to have what is known as a non-routable internal IP address such as 192.168.1.1 or 10.0.0.1 as it's address
- Below are some of the standard admin interface addresses used by some of the more common wireless router manufacturers:
- Linksys - 192.168.1.1 or 192.168.0.1
- DLink - 192.168.0.1 or 10.0.0.1
- Apple - 10.0.1.1
- ASUS - 192.168.1.1
- Buffalo - 192.168.11.1
- Netgear - 192.168.0.1 or 192.168.0.227
- Choose a strong password for the router administration GUI:
- Routers usually come with an obvious default password (admin in many cases). Therefore, it is important to change it and choses a secure password to try to prevent someone from entering to the router administration GUI and change your network configurations.
- Choose a strong password for the wireless network
- Authentication
- The final layer of protection is individual authentication.
- The standard method of WLAN authentication uses the 802.1X protocol.
- If the protocol is enabled, unauthenticated users cannot get past the AP to access the rest of the network.
- Install a good firewall device to your router
Service set
https://en.wikipedia.org/wiki/Service_set_(802.11_network)
In IEEE 802.11 wireless local area networking standards, a service set is a group of wireless network devices that are operating with the same networking parameters.
Service sets are arranged hierarchically,: Basic Service Sets (BSS) are units of devices operating with the same medium access characteristics (i.e. radio frequency, modulation scheme etc), while Extended Service Sets (ESS) are logical units of one or more basic service sets on the same logical network segment (i.e. IP subnet, VLAN etc). There are two classes of basic service sets: those that are formed by infrastructure mode redistribution points (access points or mesh nodes), and those that are formed by independent stations in a peer-to-peer ad hoc topology. Basic service sets are identified by BSSIDs, which are 48-bit labels that conform to MAC-48 conventions. Logical networks (including extended service sets) are identified by SSIDs, which serve as "network names" and are typically natural language labels.
Wireless mobile networks
Para ver las características de las tarjetas de red (network card)
http://www.linuxnix.com/find-network-cardwiredwireless-details-in-linuxunix/
Tales como: Name of network cards, Network card link status, Network card speeds, Network card MAC address, Network card IP address, Network card driver details, Network card manufacture details, Network card duplex/half duplex details, Network card auto-negotiation details, Complete network card capabilities details, Complete network card hardware details
sudo lshw -c network
DHCP
Media:DHCP-Lecture_Greg2018.pdf
DNS
Media:Introduction_to_DNS-Lecture_Greg2018 .pdf
Media:DNS-Lecture_Greg2018.pdf
Observing DNS Resolution: Media:Lab-Observing_DNS_Resolution.pdf
- Part 1: Observe the DNS Conversion of a URL to an IP Address
- Part 2: Observe DNS Lookup Using the nslookup Command on a Web Site
- Part 3: Observe DNS Lookup Using the nslookup Command on Mail Servers
Using Wireshark to observe traffic
Media:4-2-Using Wireshark to observe the DHCP process.pdf
Media:7-3-Using_Wireshark_to_Examine_a_UDP_DNS_Capture.pdf
Network simulation using Cisco-PacketTracer
Cisco - PacketTracer
Packet Tracer is a powerful network simulation program which allows students to experiment with network behavior. It supplements physical equipment in the classroom by allowing students to create a network with an almost unlimited number of devices, encouraging practice, discovery and troubleshooting.
Installation
He guardado las versiones descargadas en:
/home/adelo/1-system/1-disco_local/1-mis_archivos/1-pe/1-ciencia/1-computacion/stockage-computacion/SO-Programas
El paquete (Linux or Windows) se descarga de la página oficial de Cisco (netacad): https://www.netacad.com/group/offerings/packet-tracer
La versión 6.2 puede ser descargada aquí: https://arief-jr.blogspot.ie/2016/01/download-cisco-packet-tracer-62-for.html
Otro link para la versión 7.2 (tuve problemas para descargar el el paquete desde el sitio oficial la última vez. La descarga comenzaba muy muy lenta y luego se detenía en cierto puto): https://www.itechtics.com/download-cisco-packet-tracer-7-2/
Creé una cuenta en Cisco para poder tener acceso a PacketTracer. Contraseña: Aa16407742**
Intalación en Ubuntu:
sudo ~/Downloads/PacketTracer70/./install
Luego para porder launch packettracer in a terminal:
sudo ln -s /opt/packetTracer/packetTracer6.2-student/packettracer /usr/local/bin/packettracer6.2
Es muy importante notar que luego de la instalación de Packet Tracer, en el directorio se encontrarán dos ejecutables:
/opt/packetTracer/packetTracer6.2-student/packettracer /opt/packetTracer/packetTracer6.2-student/bin/PacketTracer6
El ejecutable adecuado es «/opt/packetTracer/packetTracer6.2-student/packettracer». El que se encuentra en la carpeta /bin también inicia la aplicación, pero por alguna razón generó problemas en la última instalación en Ubuntu 18.04. En la versión 6.2, bin/PacketTracer6 inicia la aplicación pero ésta no funciona correctametne; en la versión 7.1 bin/PacketTracer7 genera un «Segmentation fault», la aplicación crash y se cierra.
No tengo ni la más remota idea de por qué existe este otro ejecutable en la directorio /bin. Creo (no estoy seguro) que la primera vez que instalé Packet Tracer estuve usando el ejecutable de /bin para iniciar la aplicación y no generó estos problemas. Esto me trajo muchos problemas la última vez que instalé Packet Tracer porque se tiende a pensar que el ejecutable se encuentra en los directorios /bin. Es por ello que pensé que éste era el correcto y estuve dos días buscando la solución para el segmentation fault.
./PacketTracer6: error while loading shared libraries: libcrypto.so.1.0.0: cannot open shared object file: No such file or directory
64bit:
La librería «libcrypto.so.1.0.0» se encuentra es este paquete:
sudo apt-get install libssl1.0.0
Luego de la instalación, el paquete se encontrará aquí:
/usr/lib/x86_64-linux-gnu/libcrypto.so.1.0.0
Em el siguiente vídeo también proponen la instalación del siguiente paquete para la instalación de PacketTracer 7 64bit: https://www.youtube.com/watch?v=HKozuo2FmMA&vl=en
sudo apt-get install libqt5webkit5
32bit - PacketTracer6.2: Dependencies on PacketTracer6.2 use 32 bit version.
La versión 32bit de la librería «libcrypto.so.1.0.0» se encuentra en el siguiente paquete:
sudo apt-get install libssl1.0.0:i386
Luego de la instalación, el paquete se encontrará aquí:
/usr/lib/i386-linux-gnu/libcrypto.so.1.0.0
Antes de instalar la librería «libssl1.0.0:i386» realicé la siguiente instalación. No sé si es necesario pero lo hice probando otras propuestas antes de encontrar la solución. Es posible que sea también necesario completar estos pasos antes de instalar «libssl1.0.0:i386»: https://blog.teststation.org/ubuntu/2016/05/12/installing-32-bit-software-on-ubuntu-16.04/
Enable the i386 architecture (as root user):
dpkg --add-architecture i386 apt-get update
Install 32-bit libraries (as root user):
apt-get install libc6:i386 libstdc++6:i386
Al tratar de intalar PacketTracer 6.2 en Ubuntu 18.04, aunque en mi sistema se encontraba instalada la librería para 64bit, PacketTracer6.2 seguía generando el error. Luego me percaté que en el link desde el cual descargué la vesión 6.2 dice:
If using linux for installation packet tracer you must installed multilib, because dependencies on packet tracer use 32 bit version.
Por lo tanto, el problema era que no tenía la librería correspondiente para 32bit; como se propone en este forum: https://ubuntuforums.org/showthread.php?t=2218961
También instalé algunos de los paquetes mostrados en el siguiente link con el fin de solucionar este error durante la instalación de la versión 6.2 en Ubuntu 18.04. Realmente no sé si sirvió de algo porque al instalarlos no se solucionó el error; pero sigue siendo posible que también hayan contribuido a la solución del problema, aunque no creo:
https://askubuntu.com/questions/637113/unable-to-locate-package-lib32bz2-1-0
Otro error solucionado
La primera vez que lo isntalé se generó el error descrito y solucionado aquí: https://forum.ubuntu-fr.org/viewtopic.php?id=2014677
J'ai complété l'installation du logiciel puis j'ai essayé de me rendre dans le tableau de bord( dash) pour y trouver le logiciel où il ne se trouvait pas. Par ligne de commande, j'ai essayé de taper : packettracer et cela me dit simplement: "Starting Packet Tracer 7.1" et ne fait plus rien ensuite.
Donc tu ouvres un beau terminal, et tu lances :
/opt/pt/bin/PacketTracer7
Quand j'accède au fichier pour ./PacketTracer7: error while loading shared libraries: libQt5Script.so.5: cannot open shared object file: No such file or directory
Instalar:
libqt5script5
Je viens de le faire mais à l'instant mais ça ne résous pas mon cas,
je suis retourné voir le fichier /opt/pt/bin/PacketTracer7 et quand je l'ouvre, il m'indique qu'il me manque la librairie : " libQt5ScriptTools.so.5" j'ai donc essayé de refaire la même chose que précédemment en l'adaptant à la librairie , donc je tape :
sudo apt-get install libqt5scripttools5
Et maintenant, ça fonctionne quand je vais chercher le fichier /usr/pt/bin/PacketTracer7
Configuration más frecuentes using PacketTracer
- IP configuration on a PC: Click on the desktop tab, then selecting the IP configuration icon.
- Verify connectivity settings: On a PC, verify the connectivity settings by going to Desktop and clicking on command prompt. At the command prompt, type the command:
- ipconfig : To view your network device information.
- ipconfig /release :
- ipconfig /renew : To force the PC to request an IP address from the Router.
Lab 1: Configuring Wireless Access and Security
In this lab, you will configure a Linksys WRT300N (https://en.wikipedia.org/wiki/Linksys_routers#WRT300N) in Packet Tracer.
Cofigurar la conección entre el Router y la WAN / LAN
Setup the device topology diagram
- Setup the devices as shown in Figure 1:
- PC1 will be acting as the Internet connection
- PC0 and Laptop0 will be in our LAN.
- Connect a crossover cable from PC1 to the wireless router’s WAN (Internet) port and connect a straight through cable from PC0 to one of the wireless router’s LAN (Ethernet) ports.
- Podemos pensar en esta configuración de la siguiente forma: el Wireless Router podría, por ejemplo, representar el Router que se encuentra integrado en la Box de nuestra home network; al cual hemos conectado una PC0 a través de un cable y nuestra Laptop a la Wireless Network. PC1 representa cualquier PC fuera de nuestra LAN.
Configurar la conexión en PC1 y PC0
NOTA: Normalmente deberíamos configurar el Router antes de los dispositivos en la LAN. Esto porque el DHCP Server del Router asignará los IP's a nuestros dispositivos en la LAN; y las confuguraciones en el Router afectarán, por supuesto, las IP's otorgadas a los dispositivos. Sin embargo, a manera de ejercicio, y con el fin de destacar ciertos detalles, vamos primero a realizar las configuraciones en los dispositivos dentro de la LAN.
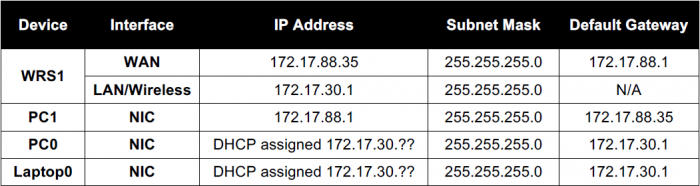
- PC1 will be acting as the Internet connection, so we need to set the IP address, subnet mask, and default gateway statically as listed in Table 1.
- Set the IP configuration on PC0 to DHCP by clicking on the desktop tab, then selecting the IP configuration icon.
- The wireless router will provide an IP address to the PC0 using the default DHCP configuration.
- Verify connectivity settings for PC0: Go to Desktop and click on command prompt. At the command prompt, type the command ipconfig to view your network device information.
- If the PC does not receive an IP address in the command prompt type ipconfig /renew, this will force the PC to request an IP address from the Router.
- Notice which IP address is the default gateway. This is the default IP address of a Linksys WRT300N. Por tanto, el Router a asignado un IP a PC0 a través de la configuración por defecto (ver Nota al inicio de esta sección).
Configurar el Router
Click on the Wirelessrouter0 and select the Setup tab for the wireless router’s GUI.
Log in
In the real world the default login credentials are a username admin and a password of: admin. Note that this is very insecure since it is the factory default and provided publicly. You will set our own password in a later task.
Configure the WAN interface
Normally an Internet Service Provider would use DHCP to give out addresses to the WAN port. For this lab, you will assign the address statically.
- Configure the WAN port to have a static IP address:
- From the Internet Connection Type pull-down menu, select Static IP and set the IP address settings for Internet Setup:
- Internet IP Address - set to: 172.17.88.35
- Subnet Mask: 255.255.255.0
- Default Gateway - set to the ISP address: 172.17.88.1
- From the Internet Connection Type pull-down menu, select Static IP and set the IP address settings for Internet Setup:
Configure the LAN IP addressing
- Set the Network Setup Address:
- Under Network Setup, enter the Router IP of 172.17.30.1 / Subnet Mask: 255.255.255.0
- NOTE: At this point you would be disconnected from the web page if you were configuring from a PC, as you just changed the IP address you are connected to. It would take a minute or two, and you would need to refresh your browser, but you should be redirected to the new URL of the web utility. If not, you would need to release your IP address and request a new one, before your navigate your browser there. You would be asked to login again.
- Under Network Setup, enter the Router IP of 172.17.30.1 / Subnet Mask: 255.255.255.0
Verify IP address changes:
La configuración de la LAN IP addressing en el Router, afectará, por supuesto, la IP Address que el DHCP Server del Router asígnará a las PC's de la LAN. Para observar dichos cambios vamos al Command prompt de PC0 y ejecutamos: ipconfig /release ipconfig /renew
Luego de esto, note la nueva IP asignada por el DHCP Server del Router.
Verify connectivity
Ping the WAN IP Address of the Wireless Router (172.17.88.35) to verify you can get to the outside of your network. The pings should succeed. If you try to Ping PC1 172.17.88.1, it may fail if your firewall won’t allow replies back in.
Wireless settings
Basic wireless wettings on the Routher
The Linksys WRT300N allows you to choose which network mode to operate in. Currently, the most common network mode for clients is Wireless-G and for routers is BG-Mixed. When a router is operating in BG-Mixed, it can accept both B and G clients. However, if a B client connects, the router must scale down to the slower level of B. For this lab, pick the fastest speed your clients can support.
On WRS1, navigate to the Wireless page:
- Set the Network Name (SSID) to WRS_1
- Wireless-N Only – Radio Band – Change to Standard – 20MHz Channel.
- Standard Channel – Leave at default
- SSID Broadcast – Leave Enabled for now.
Incorporar una Wireless Network Card a la Laptop
Por defecto, Packet Tracer no incorpora una Wireless Network Card (en este caso compatible con Linksys WRT300N) a la Laptop. Debemos entonces incorporar una antes de intentar hacer la Wireless conection.
Si intentamos verificar la conexión en la Laptop antes de incorporar la Wireless Network Card:
- Go to the Desktop tab then select the PC Wireless Icon.
... el programa desplegará el siguiente mensaje: «A WMP300N or WPC300N wireless interface is required to connect»
Para incorporar la Wireless Network Card:
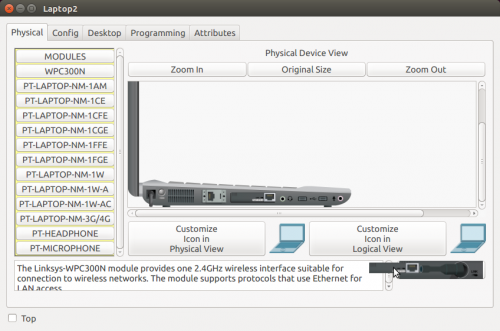
- Click on the Laptop > Physical
- Observar el diseño de la Laptop (observar los diseños de los dispositivos que presenta la Laptop) (Figure 2)
- Note que la Network Card corresponde a un puerto FastEthernet.
- Antes de realizar el cambio, debemos apagar la Laptop. Para esto haga clic en el botón que se encuentra al lado de la conexión electrica. Arriba de la luz verde que simboliza que el dispositivo se encuentra encendido. Note que luego de prescionarlo desaparece la luz verde, lo cual indica que el dispositivo se encuentra apagado. (Figure 2 and Figure 3)
- Utilizando el cursor del mouse, arraste la actual tarjeta de red (FastEthernet) hacia la esquina inferior derecha, hacia el espacio en donde se muestra el diseño de los dispositivos físicos. Note que si se ha arrastrado correctamente, el espacio en donde se encontraba la tajeta de red en la Laptop quedará libre. (Figure 3 and Figure 4)
- Ahora arrastre la tarjeta que desea instalar desde las distintas opciones que se encuentran en el panel a la derecha hacia el espacio libre en la Laptop. (Figure 4)
- En este caso debemos escoger una WPC300N. (Figure 4)
Verify wireless connection
Ahora que hemos incorporado una Wireless network card a nuestra Laptop, podemos entonces verificar la Wireless connection:
- Go to the Desktop tab then select the PC Wireless Icon. Click on the Connect Tab.
- If necessary, you may have to click on Refresh to update your wireless networks. You should see the new network (WRS_1).
- Click on the name to highlight it and then click Connect. Click on the Link Information Tab. When it is done, it will congratulate you on creating a profile (Message: You have successfully connected to the access point).
Configure DHCP Settings
Give a static DHCP binding to PC0 and Laptop0
- On Laptop0, verify connectivity settings going into cmd. At the command prompt, type the command Ipconfig /all to view your network device information. Note the Physical Address (MAC) of the Wireless Connection.
- On the Router, navigate back to the Setup page (the Basic Setup is the default tab). In the middle of the Basic Setup Page, under DHCP Server Settings, click the DHCP Reservations button. Una nueva ventana se abrirá...
- There are two ways to assign DHCP addresses:
- The first method will always assign the client the same address the client has right now.
- Find PC0 by its MAC address in the list of current DHCP clients (Hint: it should be listed as a LAN connection)
- Check the Select box next to your PC. Click Add Clients. Now PC0 will show up under Clients Already Reserved.
- This gives PC0 (in this example, the computer with a MAC address of 00:60:5C:D9:2D:1D) the same IP address it has right now (172.17.30.100) whenever it requests an address through DHCP.
- The first method will always assign the client the same address the client has right now.
- The second method to assign DHCP addresses is to select the address you want the machine to get. You will assign Laptop0 the static IP address listed in the Addressing Table, not the one it received initially.
- Under Manually Adding Client, enter your client’s actual name (puse Laptop0 aquí pero no estoy seguro) , .24 for the IP address, the actual MAC address of your PC’s Wireless Connection, and click Add. Now whenever Laptop0 connects to the wireless router, it receives the IP address 172.17.30.24 via DHCP.
- The second method to assign DHCP addresses is to select the address you want the machine to get. You will assign Laptop0 the static IP address listed in the Addressing Table, not the one it received initially.
Configure other DHCP server settings
Right underneath the DHCP Reservation are the other settings for the DHCP server.
What is the default maximum number of users the WRS300N will hand out DHCP addresses to?
- 50 users.
- Start IP Address - Change to: 172.17.30.50.
- Maximum Number of Users - Change to: 75
These settings give any PC that connects (wired or wirelessly) to this router requesting an IP address through DHCP, an address between 172.17.30.50–124. Only 75 clients at a time are able to get an IP address and they can only have the address for 24 hours, after which time they must request a new one.
Verify the static IP address change and conection
On both PC0 and Laptop0, at the command prompt, type:
Ipconfig /release Ipconfig /renew
... to verify the IP addresses you assigned are used. On Laptop0, ping the IP address of the WAN port to verify you can reach the Internet.
Lab 4: Configuring basic router settings with the Cisco IOS CLI
Cisco IOS (Internetwork Operating System) CLI (IOS Command Line Interface)
In this lab, you will build a multi-router network and configure the routers to communicate using the most common Cisco IOS configuration commands.
""" Resumen de comandos """
Al tratar de configurar un puerto serial en el cual conecté un cable serial DTE:
clock rate 250000
This command applies only to DCE interfaces
enable
#configure terminal
""""""""""""""""""""""""""""""""
(config)#hostname R1
""""""""""""""""""""""""""""""""
(config)#line console 0
(config-line)#password cisco
(config-line)#login
(config-line)#exit
""""""""""""""""""""""""""""""""
(config)#line vty 0 4
(config-line)#password cisco
(config-line)#login
(config-line)#exit
""""""""""""""""""""""""""""""""
(config)#enable password cisco
(config)#enable secret class
""""""""""""""""""""""""""""""""
(config)#banner motd #Unauthorized Use Prohibited#
""""""""""""""""""""""""""""""""
(config)#no ip domain-lookup
""""""""""""""""""""""""""""""""
(config)#line console 0
(config-line)#logging synchronous
""""""""""""""""""""""""""""""""
show ip interface brief
""""""""""""""""""""""""""""""""
(config)#interface serial 0/0/0
(config-if)#description WAN link to R2
(config-if)#ip address 172.17.0.1 255.255.0.0
(config-if)#clock rate 64000
(config-if)#no shutdown
(config-if)#exit
#show interfaces serial 0/0/0
""""""""""""""""""""""""""""""""
(config)#interface FastEthernet 0/0
(config-if)#description R1 LAN Default Gateway
(config-if)#ip address 172.16.0.1 255.255.0.0
(config-if)#no shutdown
(config-if)#exit
#show interfaces FastEthernet 0/0
""""""""""""""""""""""""""""""""
#copy running-config startup-config
""""""""""""""""""""""""""""""""
#show running-config
Configuring basic router settings
Utilizaremos un Router-PT (Generic)
In real life tenemos que conectar un console cable from a computer to the router para poder hacer las configuraciones en el Router. Sin embargo en Packettracer podemos simplemente hacer clic en el routar y acceder al CLI.
- Click on the Router > CLI:
Would you like to enter the initial configuration dialog? No (para así entrar a la línea de comandos desde el inicio, sin que el sistema nos proponga las opciones de configuración automáticamente).
Enter privileged EXEC mode
Router> Router>enable Router#
El comando «enables» is used to enter privileged EXEC mode. Como el Router aún no ha sido configurado, éste no solicita un password luego del comando «enable». Ya veremos como configurar un password. Note que luego de ingresar el comando «enable» aparece un # que indica que estamos en privileged EXEC mode.
Access global configuration mode
Router#configure terminal Router(config)#
El comando «configure terminal» is used to access global configuration mode. This command can only be used in privileged EXEC mode.
Ya estando en el «global configuration mode» podemos empezar las configuraciones:
Configure a host name
Router>enable Router#configure terminal Router(config)#hostname R1 R1(config)# // Después de configurar el host name, nuestra línea de comandos se verá así
Configure a console password and enable login
Este es el password que será requerido al ingresar al CLI.
R1(config)#line console 0 R1(config-line)#password cisco // "cisco" will be our console password R1(config-line)#login R1(config-line)#exit R1(config)#
Configure the password on the vty lines
R1(config)#line vty 0 4 R1(config-line)#password cisco R1(config-line)#login R1(config-line)#exit
Configure the enable and enable secret passwords
R1(config)#enable password cisco // "cisco" will be our enable password R1(config)#enable secret class // "class" will be our enable secret password
The «enable secret password» es el que será requerido al ingresar el comando «enable» (to enter privileged EXEC mode).
Note: Remember that the enable secret password is encrypted when viewing the configuration. Also do not type enable secret password class. If you do, the secret password will be password, not class. The enable secret password takes precedence over the enable password. When an enable secret password is configured, the enable password is no longer accepted. It will be necessary to enter the enable secret password to enter privileged EXEC mode. Some network administrators may choose to configure only the enable secret password.
Configure a message-of-the-day (MOTD) banner
When a user connects to the router, the MOTD banner appears before the login prompt. In this example, the number sign (#) is used to start and end the message. The # is converted to ^C when the running-config is displayed.
R1(config)#banner motd #Unauthorized Use Prohibited#
Configure the router to not attempt to resolve host names using a DNS server
If this is not configured, the router assumes that any mistyped command is a host name and attempts to resolve it by looking for a DNS server. On some routers, it can take considerable time before the prompt returns.
R1(config)#no ip domain-lookup
Console messages do not interfere with command input
Configure the router so that console messages do not interfere with command input. This is helpful when exiting configuration mode, because it returns you to the command prompt and prevents having messages from breaking into the command line.
R1(config)#line console 0 R1(config-line)#logging synchronous
Configure the serial interface
In global configuration mode, configure serial interface 0/0/0 on R1:
R1(config)#interface serial 0/0/0 R1(config-if)#description WAN link to R2 R1(config-if)#ip address 172.17.0.1 255.255.0.0 R1(config-if)#clock rate 64000 R1(config-if)#no shutdown R1(config-if)#exit
Note: Enter the clock rate only on the router serial interface to which the DCE interface end of the cable is attached. The cable type (DTE or DCE) is printed on the outside of each end of the null serial cable. When in doubt, enter the clock rate command on both router serial interfaces. The command is ignored on the router to which the DTE end is attached. The no shutdown command turns on the interface. The shutdown command turns the interface off.
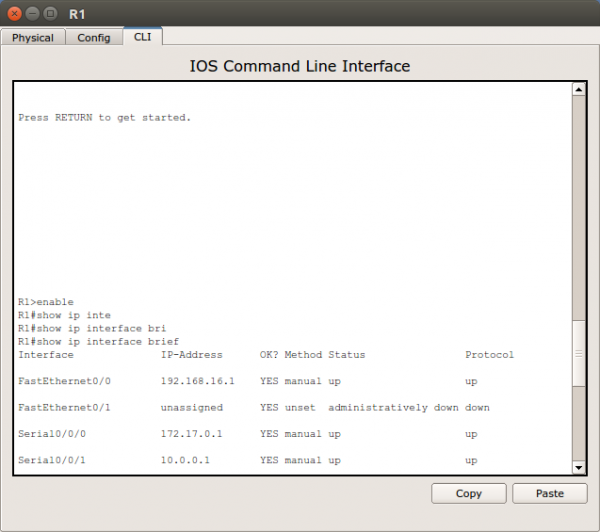
Display information about the serial interface
Enter the show interfaces command on R1:
R1#show interfaces serial 0/0/0
Serial0/0/0 is down, line protocol is down
Hardware is PowerQUICC Serial
Description: WAN link to R2
Internet address is 172.17.0.1/16
MTU 1500 bytes, BW 128 Kbit, DLY 20000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation HDLC, loopback not set
Keepalive set (10 sec)
Last input never, output never, output hang never
Last clearing of "show interface" counters 00:01:55
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
6 packets output, 906 bytes, 0 underruns
0 output errors, 0 collisions, 3 interface resets
0 output buffer failures, 0 output buffers swapped out
0 carrier transitions
DCD=down DSR=down DTR=up RTS=up CTS=down
What did you discover by issuing the show interfaces command
- Serial 0/0/0 status is:
- Line protocol is:
- Internet address:
- Encapsulation:
- If the serial interface was configured, why did the show interfaces serial 0/0/0 indicate that the interface is down?
Configure the Fast Ethernet interface
In global configuration mode, configure the Fast Ethernet 0/0 interface on router R1:
R1(config)#interface FastEthernet 0/0 R1(config-if)#description R1 LAN Default Gateway R1(config-if)#ip address 172.16.0.1 255.255.0.0 R1(config-if)#no shutdown R1(config-if)#exit
Note: Ethernet interfaces do not have a DTE or DCE distinction; therefore, it is not necessary to enter the clock rate command.
Display information about the Fast Ethernet interface
Enter the show interfaces command on R1:
R1#show interfaces FastEthernet 0/0
FastEthernet0/0 is up, line protocol is up
Hardware is AmdFE, address is 000c.3076.8460 (bia 000c.3076.8460)
Description: R1 LAN Default Gateway
Internet address is 172.16.0.1/16
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Auto-duplex, Auto Speed, 100BaseTX/FX
ARP type: ARPA, ARP Timeout 04:00:00
Last input never, output 00:00:18, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog
0 input packets with dribble condition detected
52 packets output, 5737 bytes, 0 underruns
0 output errors, 0 collisions, 1 interface resets
0 babbles, 0 late collision, 0 deferred
52 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
What did you discover by issuing the show interfaces command
- Fast Ethernet 0/0 status is:
- Line protocol is:
- Internet address:
- Encapsulation:
- To which OSI layer is the encapsulation referring?
- Why did the show interfaces FastEthernet 0/0 command show that the interface is up?:
Save the configuration
Save the running configuration to the startup configuration from the privileged EXEC prompt.
R1#copy running-config startup-config
Note: Save the running configuration for the next time that the router is restarted. The router can be restarted either by a software reload command or a power cycle. The running configuration is lost if it is not saved. The router uses the startup configuration when the router is started.
View the router running configuration
From the privileged EXEC prompt:
R1#show running-config //This command can be abbreviated as sh run
Este comando muestra todas las configuraciones llevadas a cabo:
*** Some output omitted ***
Building configuration...
Current configuration : 605 bytes
!
hostname R1
!
enable secret 5 $1$eJB4$SH2vZ.aiT7/tczUJP2zwT1
enable password cisco
!
no ip domain lookup
!
interface FastEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface Serial0/0
no ip address
shutdown
!
banner motd ^CUnauthorized Use Prohibited^C
!
line con 0
password cisco
logging synchronous
login
line aux 0
line vty 0 4
password cisco
login
!
endNote que el «enable cisco password» es el único password encrypted.
Lab 5: Configuring Challenge Handshake Authentication Protocol Bi-directional
- PPP: point to point.
- CHAP: Challenge Handshake Authentication Protocol. Is'a PPP authentication protocol.
In this lab we will learn:
- How to configure CHAP on routers.
- How to set PPP encapsulation on routers
CHAP is the authentication options requiring that the calling side of the link, the peer, enter authentication information to help ensure that the user has the network administrator's permission to make the call. In this lab, however, two-way authentication will be used. Therefore, each router requires the peer router to authenticate.
CHAP does not itself prevent unauthorized access; it merely identifies the remote end. The router or access server then determines whether that user is allowed access.
When configuring PPP authentication, you can select:
- Challenge Handshake Authentication Protocol (CHAP) or,
- Password Authentication Protocol (PAP).
In general, CHAP is the preferred protocol:
- Because CHAP offers features such as periodic verification to improve security; this makes CHAP more effective than PAP because CHAP requires a challenge before authentication can take place.
- CHAP is used to periodically verify the identity of the remote node, using a threeway handshake. This is done upon initial link establishment and can be repeated any time after the link has been established.
- Also, CHAP passwords are a shared secret and are not sent over the line in clear text like PAP.
Initial configuration of the Network
Antes de realizar la configuración CHAP, vamos a conectar dos routers (Generic Router PT) y realizar las configuraciones básicas aprendidas en el Lab 4.
- Conecte dos Routers a través de un cable serial DCE.
- Sería apropiado (aunque no indispensable para este lab) realizar todas las configuraciones básicas aprendidas en el lab 4. Las que sí son indispensables para este lab son:
- - Renombre los router como: Lab_A y Lab_b
- - Configure las interfaces correspondientes (en donde se conectó el cable serial) en cada Router:
Lab_A(config)#interface serial 0/0/0 Lab_A(config-if)#ip address 192.168.1.1 255.255.255.0 Lab_A(config-if)#no shutdown Lab_A(config-if)#clock rate 250000 Lab_B(config)#interface serial 0/0/0 Lab_B(config-if)#ip address 192.168.1.2 255.255.255.0 Lab_B(config-if)#no shutdownNote que el clock rate ha sido establecido sólo en Lab_A...
- Ensure connectivity by pinging between routers...
Define username and password to expect from the remote router
Lab_A(config)#username Lab_B password clavechap
Lab_B(config)#username Lab_A password clavechap
username is the peer router’s name and the password is a shared password between Lab_A and Lab_B.
Configure the interface on for PPP encapsulation
Lab_A(config)#interface serial 0/0/0
Lab_A(config-if)#encapsulation ppp
Repetir en Lab_B
See which ppp authentication options are available
Lab_A(config-if)#ppp authentication ?
La orden alterior (?) retorna las ppp authentications available.
Now configure for CHAP authentication
Lab_A (config-if)#ppp authentication chap
Repetir en Lab_B
Ensure connectivity by pinging between routers...
Troubleshooting / debugging
En esta sección aprenderemos como detectar problemas de conectividad. Para ello vamos a utilizar debug command
- Enable debugging on both routers with the command:
Lab_A#debug ppp authentication Lab_B#debug ppp authentication
- Cuando activamos debug command, el sistema automáticamente imprimirá información en el CLI (debug output) cuando detecte irregularidades.
- The router continues to generate such output until you enter the corresponding no debug command (in this case, the no debug ppp authentication command). En caso de que hayamos activado distintos debug commands, to stop all debug messages usamos el comando no debug all
- Delete the serial link between the two routers by deleting the cable from S0/0/0 on either router. Wait for the interface to go into a down state before proceeding to next step.
- Plug a serial cable back in from Lab_A to Lab_B to reestablish the connection and view the debug output of CHAP authentication.
- Ensure to place the clocking side in Lab_A. El clocking side es indicado con un la imagen de un reloj en el cable.
- Al conectar el cable se debe generar automáticamente el debug output en el CLI. Does the output indicate success or failure?
- Now delete the username or password on both routers:
Lab_A(config)#no username name password password
- Configure an incorrect username or password on both routers:
Lab_A(config)#username wrong_name password wrong_password
- Shutdown the interface:
Lab_A(config)#interface serial 0/0/0 Lab_A(config-if)#shutdown
- Then start the interface back up and view the authentication process displayed in the debug output:
Lab_A(config-if)#no shutdown
- Does the debug output indicate success or failure? How would this output help to solve authentication problems?
Lab 6: Configuring and verifying static routes
objectives: Implement Static routing and verify that network routes working properly.
Static routing is one method of telling routers where to send traffic. Knowledge of static routes and how to configure them using the Cisco IOS CLI is essential to success as a network technician. In this lab, you build a multi-router network and use static routing to manually create routes, so hosts on remote networks can communicate.
When configuring static routes on the routers we need to specify either:
- The next-hop IP address OR
- The exit interface of the Router
In this lab, we will specify the next hop IP address.
""" Resumen de comandos """
>show ip route
>show ip route static
>show ip route connected
(config)#ip route 192.168.0.0 255.255.255.0 172.16.10.5
If you make a mistake with the route:
(config)#no ip route 192.168.0.0 255.255.255.0 172.16.10.5
Undos the configuration of a static route to the 192.168.0.0/24 network sending traffic to a router interface with an address of 172.16.0.5
Extension Task:
- How many valid ip addresses can be used on the WAN between router 1 and router 2 as the subnet mask is 255.255.255.224. Are all of these ddresses necessary? Suggest another mask that wastes fewer addresses.
Lab: Dynamic routing
Dynamic IP route configuration: RIP v2
router rip
version 2
network 192.168.1.0
network 192.168.4.0
network 192.168.5.0
no auto-summary
"Éstas son las redes conectadas al Router. Con estos comandos le estamos diciendo a R1 que comparta sus redes con los routers vecinos"
Es muy importante notar que la dirección de la network que será introducida dependerá de la network class (A, B, C). Por ejemplo, si una interface presenta la siguiente configuración: 10.1.1.9 255.255.255.252, se deduce que la network correspondiente es: 10.1.1.8/30; sin embargo, debido a que 10.1.1.8 es una network clase A: Class A: 0 - 127 (255.0.0.0), debemos entonces introducir: network 10.0.0.0
Si queremos elimitar una network:
no network 192.168.5.0
Configuring DHCPv4 on a Router
Media:5-configuring DHCPv4 on a Router using packettracer.zip
"Specifies the range of addresses not to be leased out to clients:"
Router(config)#ip dhcp excluded-address 192.168.0.1 192.168.0.9
"Creates a DHCP pool named in this case CCT. The name can be anything of your choosing:"
Router(config)#ip dhcp pool CCT
"Defines the range of addresses to be leased:"
Router(dhcp-config)#network 192.168.0.0 255.255.255.0
"Defines the address of the default router for the client:"
Router(dhcp-config)#default-router 192.168.0.1
"Defines the address of the Domain Name Server for the client:"
Router(dhcp-config)#dns-server 8.8.8.8
"Defines the domain name for the client (Not support in PacketTracer):"
Router(dhcp-config)#domain-name fakedoaminname.com
Part 1: Build the Network and Configure Basic Device Settings
Cable the network as shown in the topology
Initialize and reload the routers and switches
Add serial interfaces
Configure basic settings for each router
hostname R1
no ip domain-lookup
service password-encryption
enable secret class
banner motd #Unauthorized access is strictly prohibited.#
line con 0
password cisco
login
logging synchronous
line vty 0 4
password cisco
login
Configure the IPv4 addresses on the router as shown in the topology
interface G0/0
ip address to 192.168.0.1 255.255.255.0
.
.
.
"Configure the clock rate for the Serial interface:"
clock rate 128000
Configure dynamic, default, and static routing on the routers
Configure RIPv2 for R1
R1(config)# router rip
R1(config-router)# version 2
R1(config-router)# network 192.168.2.252
R1(config-router)# network 192.168.0.0
R1(config-router)# network 192.168.1.0
R1(config-router)# no auto-summary
Configure RIPv2 and a default route to the ISP on R2
R2(config)# router rip
R2(config-router)# version 2
R2(config-router)# network 192.168.2.252
R2(config-router)# default-information originate
R2(config-router)# exit
R2(config)# ip route 0.0.0.0 0.0.0.0 209.165.200.225
The above configuration in b) firstly sets up rip version 2 for the network 192.168.2.0. Then using the line default-information originate command, it tells the router if the IPv4 routing table has a default route in it, advertise a default route with RIP.
IOS allows the configuration of a static default route by using special values for the subnet and mask fields in the ip route command: 0.0.0.0 0.0.0.0. For example the command ip route 0.0.0.0 0.0.0.0 209.165.200.225 creates a static default route on R2 – a route that matches all IP packets and sends those packets out to the next hop of the ISP router.
Configure a summary static route on ISP to reach the networks on the R1 and R2 routers
ISP(config)# ip route 192.168.0.0 255.255.252.0 209.165.200.226
Verify network connectivity between the routers
Verify the host PCs are configured for DHCP
Part 2: Configure a DHCPv4 Server and a DHCP Relay Agent
Configure DHCPv4 server settings on router R2
R2(config)# ip dhcp excluded-address 192.168.0.1 192.168.0.9
R2(config)# ip dhcp excluded-address 192.168.1.1 192.168.1.9
R2(config)# ip dhcp pool R1G1
R2(dhcp-config)# network 192.168.1.0 255.255.255.0
R2(dhcp-config)# default-router 192.168.1.1
R2(dhcp-config)# dns-server 209.165.200.225
"***Unfortunately, the below tasks will not work in PT 6.2. Skip these.
R2(dhcp-config)# domain-name ccna-lab.com
R2(dhcp-config)# lease 2
"
***
Continue...
R2(dhcp-config)# exit
R2(config)# ip dhcp pool R1G0
R2(dhcp-config)# network 192.168.0.0 255.255.255.0
R2(dhcp-config)# default-router 192.168.0.1
R2(dhcp-config)# dns-server 209.165.200.225
"
R2(dhcp-config)# domain-name ccna-lab.com
R2(dhcp-config)# lease 2
"
Configure R1 as a DHCP relay agent
R1(config)# interface g0/0
R1(config-if)# ip helper-address 192.168.2.254
R1(config-if)# exit
R1(config-if)# interface g0/1
R1(config-if)# ip helper-address 192.168.2.254